The Infinite Noise TRNG is an affordable and secure true random number generator (TRNG). It’s based on a modular entropy multiplier technique that continuously loops over previous random output, gathering randomness from the noise of the hardware components along the way, to generate the next random output. This way it produces a constant, measurable level of entropy which is then whitened to produce true random numbers. The openness of the implementation makes it easy to inspect and verify, as all security hardware should be!

- When you operate many virtual machines, lack of entropy can be a serious problem as all VMs share the host’s entropy source. The Infinite Noise will provide lots of random numbers to the host system.
- Large web-servers doing SSL encryption can be sped up by using hardware random number generators, while making communications more secure.
- If you operate Linux-based WiFi access points (whether using a PC, laptop, or custom hardware), they can benefit from plentiful available entropy, as WPA2 authentication relies on it.
The next big thing about random number generators is security. When you take a close look at the last 20 years of information technology, there have been dozens of security incidents with flaws in random number generators.
- 1994: First Netscape SSL implementations using a predictable seed.
- 2007: Reverse engineering showed that the Windows 2000/XP random number generator had a bug that makes it vulnerable. It’s been there for years.
- 2008: Members of the CCC developed an attack overcoming a poor RNG used in MIFARE Crypto-1, which is still used in some RFID tags.
- 2008: The random number generator used in OpenSSL had a critical bug - possibly affecting the security of all keys generated before 2008.
- 2013: Snowden documents unveiled that the Dual_EC_DRBG algorithm has been backdoored by the NSA as part of the Bullrun project. Even worse - it has been recommended by the NIST and actually adopted by manufacturers. At the same time discussions concerning the use of Intel’s RdRand (previously named: Bull Mountain [1]) in the Linux kernel came up. Doesn’t that name sound alarming enough? But even worse - there seem to be ways to let it produce not-so-random numbers. [2]
- 2016: The Linux driver for a very common wireless card (ath9k) appears to have a HWRNG which was not designed to be used as security device. Its just an ADC - and nobody knows where the data comes from. But one thing is for sure: It’s not very random and dominated the Linux entropy pool - which is really bad. Thats why kernel developers decided to disable it by default - but the change did not arrive in all distros yet.
- Building your own certificate authority
- Administering wireless access points with WPA2
- Running a high-traffic server with SSL enabled
- Having fun with one-time pads
- Replacing /dev/urandom with a more secure and faster /dev/random
- In need of a strong password
How it works:
The hardware derives entropy from thermal noise, like many random number generators. What divides it from other TRNGs is the modular entropy multiplication technique.Thermal noise of resistors is being amplified in an infinite loop to generate data – which is not totally random yet. By using modular entropy multiplication there is some correlation of adjacent bits in the stream.Health monitoring of important parameters of the raw datastream is implemented in the devices driver, which then uses the SHA-3 hashing function for cryptographic whitening to produce true random numbers.


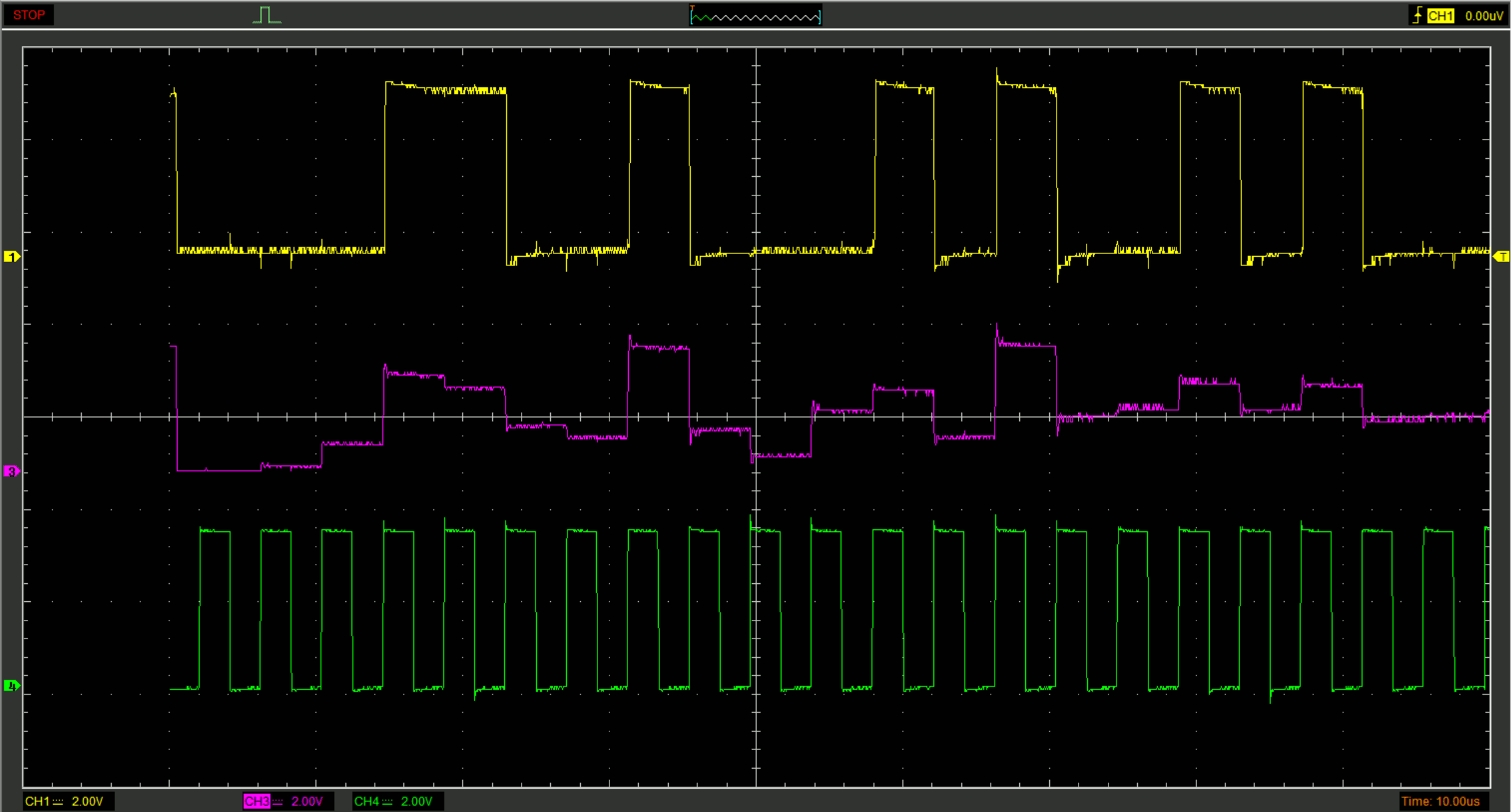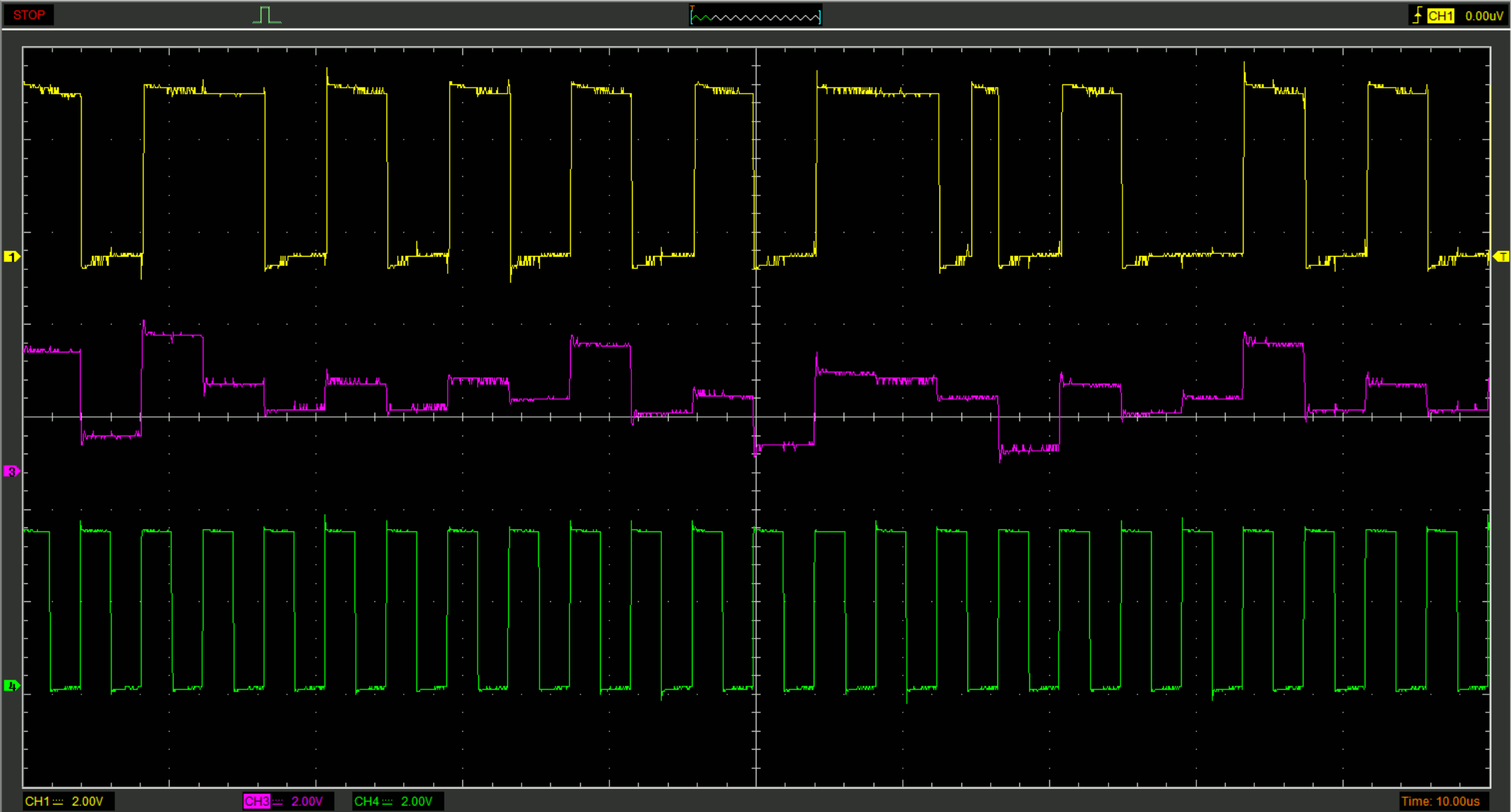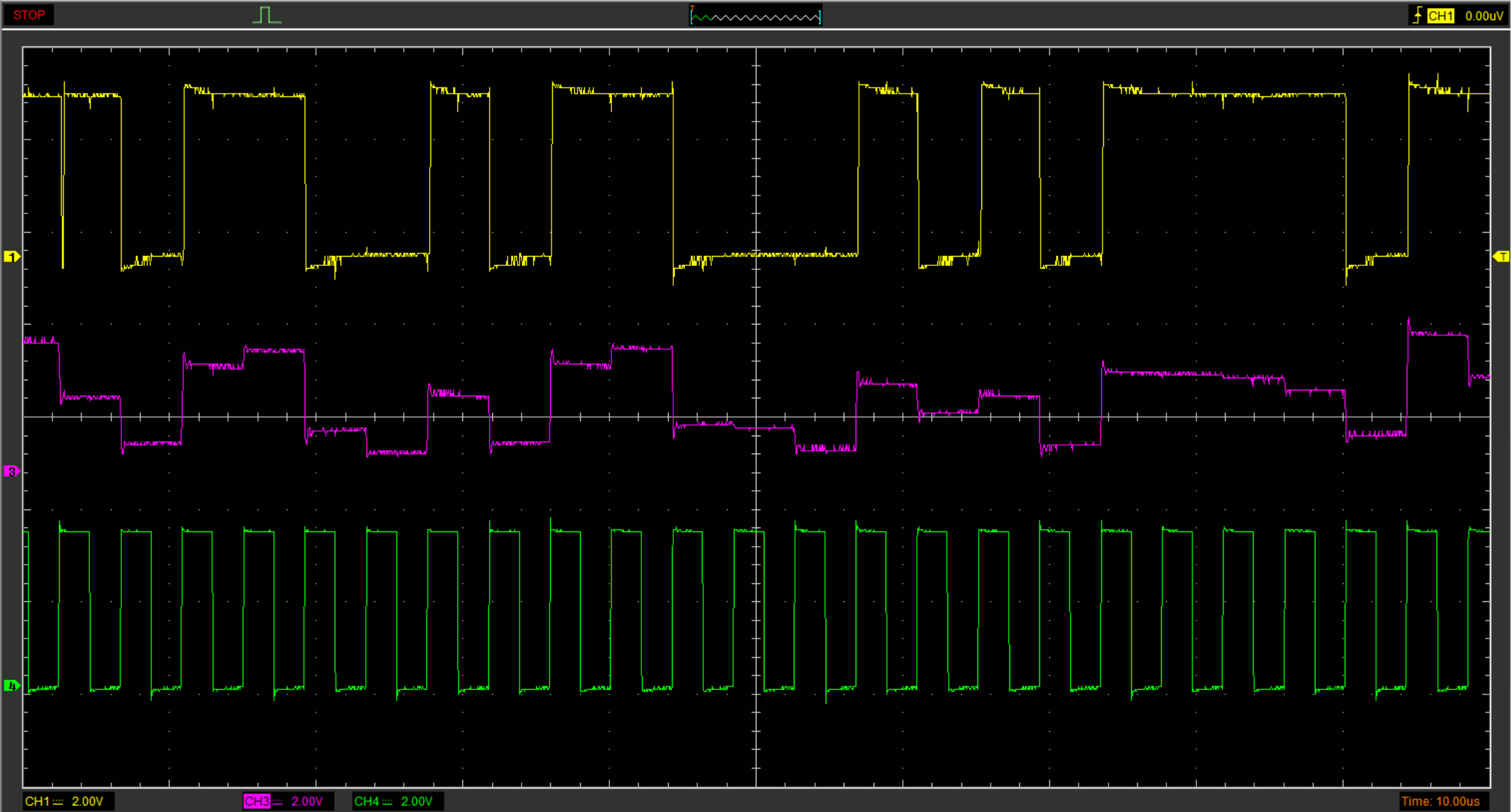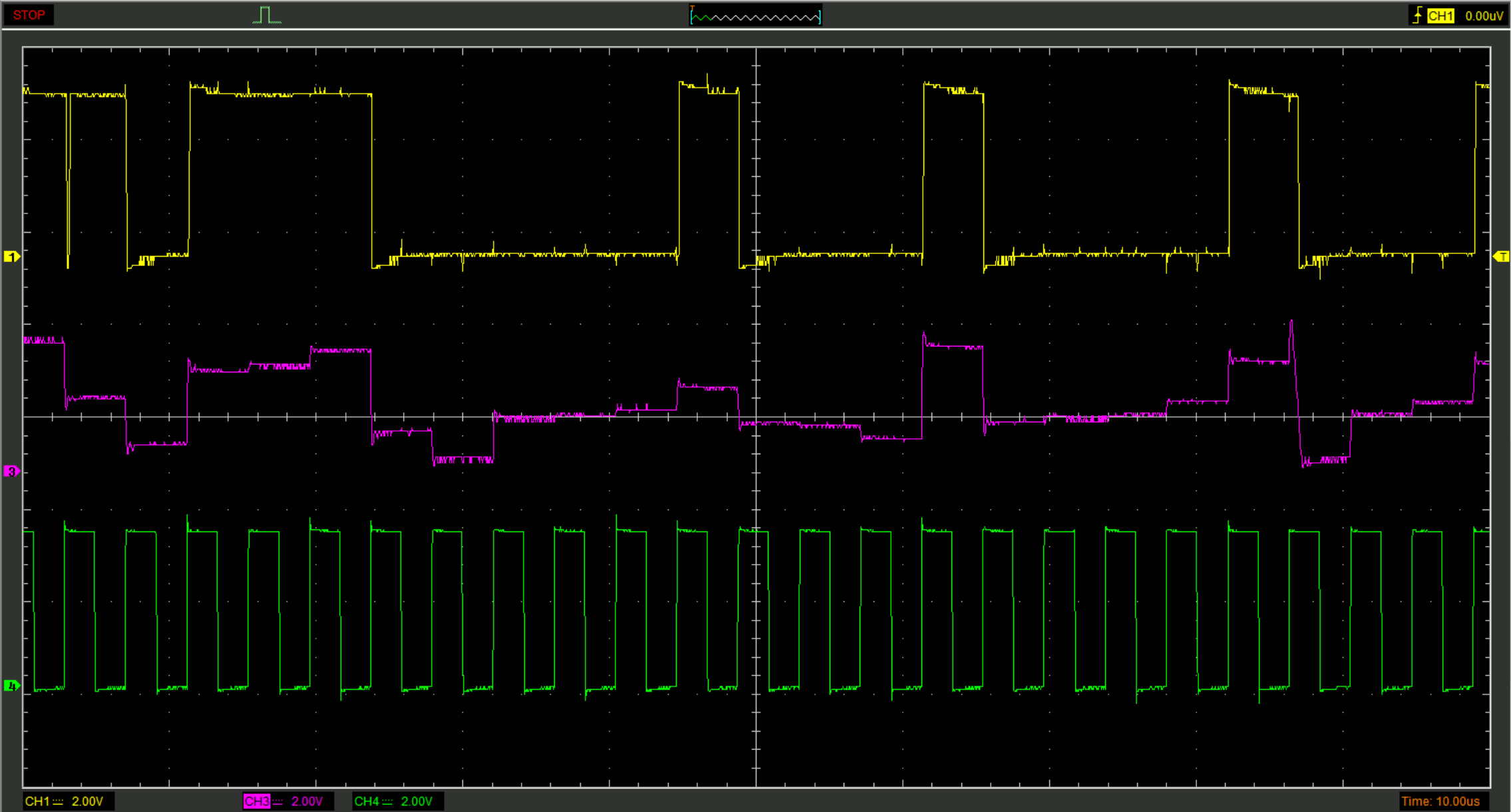
- Channel# Connected to Signal Multiplier#
- 1 COMP1 Digital 1
- 3 C8 Analog 1
- 4 SWEN1 Clock signal 1
- Random output: Default 30 KB/second of random data
- Interface: USB2.0
- Supported platforms: (Windows, Linux, and also ARM-support)
- Low Power: 8 mA
- Weight: 10 g
- Dimensions: 15 mm x 50 mm x 8 mm
- No firmware
- Uses off-the-shelf components
- SHA3-“Whitening” and health monitor built into host drivers
- Fully open source (see GitHub repo) and OSHWA-certified (#DE000006)
Custom Security Seals (5K)Stretch Goals
When the campaign surpasses the $5000 goal, every device (with enclosure) will be sealed with security seals with its serial number imprinted on them, thus making the device tamper-evident in terms of FIPS. In my opinion, it’s already pretty evident without them, as you can see in this image of one of my prototypes which needed a repair once.
In any case, by using modular entropy multiplication, the Infinite Noise TRNG is very robust against hardware attacks, as the driver will detect changes in the behaviour of the device.Thus, the best way to verify its correct operation is to use our signed driver packages - or compile it yourself after you’ve checked the code integrity - and use the --debug parameter to take a look at the raw data. Or just run the testsuite available on GitHub (manual interpretation required!)
Package Contains:
1 x Infinite Noise TRNG
Infinite Noise TRNG - True Random Number Generator
- Brand: Crowd Supply
- Product Code: CS-Infinite-Noise-TRNG
- Reward Points: 50
- Availability: In Stock
- रo 4,961.00
-
रo 4,167.00
- Price in reward points: 4961
-
- 3 or more रo 4,922.00
- 6 or more रo 4,533.00
- 14 or more रo 4,299.00
- 28 or more रo 4,190.00
Related Products
USB Security Key - 2-Factor Authentication Nano Dongle
AuthentiKator is a secure dongle implementing standard two factor authentication protocols. It is co..
रo 955.00 रo 1,275.00